Horizon Image Management on AHV

Overview
If you haven't already, check out my post on Horizon architecture on AHV, which highlights the key architectural differences between running Horizon on ESXi versus AHV, and describes the lab environment used for testing.
There are many ways to deploy and configure images and applications in a Horizon environment. Many organizations use App Volumes to deliver applications separately from the base image, and I'll cover that in a future post. For now, this post focuses on the fundamentals: building and maintaining a golden image for non-persistent and persistent desktop pools with applications baked directly into the image.
Here's my complete process for building, maintaining, and updating golden images for Horizon desktop pools on AHV.
A key lesson learned: Coming from ESXi, where you point desktop pools directly at a golden image VM and manage updates through snapshots, I initially assumed AHV's template versioning would work similarly by maintaining a single template with new versions as the pool evolved. That's not how it works. With AHV, the workflow still centers around the golden image VM and its recovery points, but each update requires creating a new template from the updated golden image. Instead of updating pools by selecting different snapshots of the same VM, you push changes by creating new templates from new recovery points. It's a different mental model, but once you understand it, the process is straightforward.
The Golden Image Process
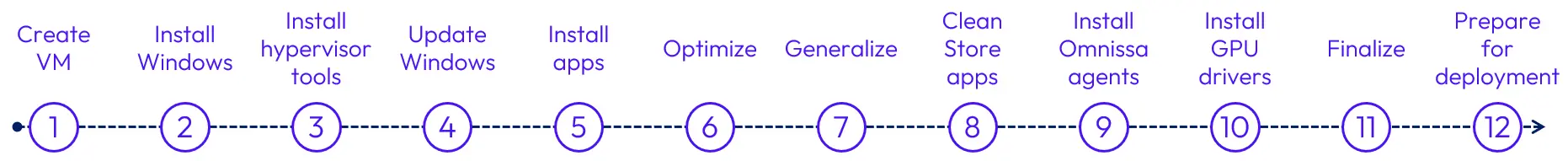
The diagram below, from the Omnissa TechZone guide, outlines the typical procedure for building and maintaining a golden image. This post walks through each phase: the initial Day Zero build, ongoing Day Two updates, and pushing changes to desktop pools.
Day Zero: Building Your Golden Image
This is where the initial Windows 11 golden image gets set up from scratch. Taking time here is worthwhile because a solid foundation makes everything else easier.
Deploy and Configure the Base VM
Start by creating the VM in Prism Central. The Windows 11 ISO needs to be imported to the Images store first. When configuring the VM, use a SCSI disk bus type, enable Secure Boot, and attach a vTPM.
Note on vTPM: There's conflicting information about whether Windows 11 actually requires a vTPM during installation. Some documentation and users report it as mandatory, while others have successfully installed without it. Your mileage may vary depending on the specific Windows 11 build and installation media. I attach it during installation as a precaution. The vTPM gets removed later before templating anyway, and Horizon will add new individual vTPM devices to each clone during provisioning.
A tip from the Omnissa TechZone guide: consider allocating more CPU and memory than planned for the clones. This speeds up Windows installation, app deployment, and optimization. The resources can be reduced later.
When using a standard Windows ISO, the Nutanix VirtIO ISO is also needed since the Windows installer won't see the SCSI disk without the drivers. Add a second CD-ROM drive to the VM and mount the VirtIO ISO alongside the Windows ISO. During installation, click Load Driver, browse to the appropriate Windows version folder on the VirtIO ISO, and select the Nutanix VirtIO SCSI pass-through controller. Alternatively, I like to use a slipstreamed ISO with VirtIO drivers already embedded, which I wrote about previously. With a slipstreamed ISO, the vDisk is detected automatically and the manual driver loading step is not necessary.
At the Windows OOBE (Out-of-Box Experience) screen, enter Audit Mode by pressing Ctrl+Shift+F3. This is critical because it prevents Windows from creating a default user profile and keeps the image clean for sysprep later. Note that every reboot while in Audit Mode will prompt with the Sysprep dialog, so just cancel it each time.
Install VirtIO Drivers
Once Windows is installed, the VirtIO drivers need to be installed for proper device support. There are two options here:
- Install just the VirtIO drivers by running the Nutanix-VirtIO installer from the mounted ISO
- Install NGT without cluster registration, which includes the VirtIO drivers plus additional guest tools
I typically install NGT for the VirtIO drivers, but do not register the VM to the cluster. The Omnissa documentation warns against installing NGT in golden images, but the concern is really about cluster registration. The golden image shouldn't be registered as a managed guest. Installing NGT without registration provides the drivers needed without the complications.
Initial Windows Configuration
Run Windows Update until no more updates are available. If the applications need it, consider installing .NET Framework 3.5 as well. The Finalize task later will precompile the .NET libraries so each clone doesn't have to.
BGInfo can provide helpful details on the desktop for troubleshooting, but it has a history of security concerns for some organizations. If the security team is comfortable with it, apply BGInfo as part of the base image configuration.
It's also important to disable Device Encryption and BitLocker. This is critical for VDI and can cause sysprep failures if left enabled. Recent Windows 11 versions may enable device encryption automatically during installation. To disable it manually:
1manage-bde -off C:
Then stop and disable the BitLocker service to prevent it from re-enabling.
This should be disabled at the image level rather than relying solely on Group Policy, since BitLocker can significantly impact storage usage with clones. Group Policy can be used as an additional enforcement layer under Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption, but disabling it in the golden image ensures the clones don't inherit any encryption overhead.
Install Applications
Install all the standard applications. This is the opportunity to bake in everything users need. For non-persistent VMs, disable auto-update functionality in applications. Also consider disabling hardware graphics acceleration in apps like Chrome if GPUs won't be used.
A note on Windows Updates for automated pools: For non-persistent desktops, Windows Update should be disabled in the golden image since updates won't persist after logoff anyway and can cause unnecessary resource consumption. Updates should instead be applied to the golden image during scheduled maintenance windows. For persistent automated pools, the approach depends on the organization's patching strategy, but many choose to manage updates through the golden image as well to maintain consistency across the pool.
First Optimization Pass
Run the Horizon OS Optimization Tool (OSOT), which still works great for Horizon on AHV. Run Analyze to review the recommended optimizations, configure the options (for persistent VMs it may be preferable to keep Windows Update and Search enabled), then run Optimize and reboot.
Take a recovery point now! This is the safety net before generalization. If anything goes wrong in the next steps, it's possible to roll back to this known-good state.
Generalize and Clean Up
Use OSOT to run Generalize (set the time zone, input locale, and system locale first) and let it reboot. This prepares Windows for sysprep. Wait a minute or two after the first login in OOBE mode for AppX package provisioning to complete.
Next, remove any unwanted Store apps. Windows 11 may re-enable Copilot and BingSearch after generalization (and potentially others as Windows updates roll out), but I've had good luck removing these two to avoid sysprep failures during pool provisioning:
1Get-AppxPackage -name Microsoft.Copilot | Remove-AppxPackage
2Get-AppxPackage -name Microsoft.BingSearch | Remove-AppxPackage
If sysprep issues come up later, check the log at C:\Windows\System32\Sysprep\Panther\setupact.log for details.
Install Agents
Install the agents in this specific order, rebooting after each:
- Horizon Agent: When installing the Horizon Agent on an AHV VM, there are specific configuration requirements:
- Select the option "This machine will be used as a Golden Image"
- Ensure the Instant Clone Agent feature is selected for installation
- Register the agent instance with a Horizon Connection Server
- Consider enabling Horizon Performance Tracker for useful performance data points
- Other features like USB Redirection, Scanner Redirection, etc. should be enabled based on specific use case requirements
- FSLogix or other third-party agents
- App Volumes Agent if using App Volumes (this must always be installed last)
After the agents are installed, run Finalize via OSOT. This performs cleanup tasks including native image generation, NTFS compression, and zeroing empty disk space. Note that some jobs like Compact can take a while to complete.
Prepare for Templating
Shut down the VM and create another recovery point. This is the completed golden image state.
Before converting to a template, optimize the VM hardware by removing unnecessary devices. CD-ROM drives are generally not used in a VDI environment, so I remove those along with the USB controller and SATA controller. Most importantly, remove the vTPM. This is required to export or clone the VM. Don't worry, the Horizon pool provisioning process will add new individual vTPM devices to each clone.
Finally, convert the VM to a template in Prism Central.
Desktop Pool Provisioning
With the template ready, you're ready to provision desktop pools in Horizon Console. The snapshot (recovery point) selected during pool creation must point to the active version of the golden image template. I'll cover the details of creating and managing desktop pools in my next post on Desktop Pools on AHV.
Day Two: Updating Your Golden Image
When it's time for updates (patches, new apps, etc.), the process is much simpler than day zero.
Power on the golden image VM (not the template). If things were set up correctly, it will be automatically logged in as the administrator account (the generalization process enables auto-login). If the Sysprep dialog pops up on login, you're still in Audit Mode and need to complete the generalization process. Install Windows updates, update applications, and add any new software as needed.
If you need to update Windows, you may need to re-enable Windows Update via OSOT first, then disable it again when done. After any updates, run Optimize again (updates may re-enable services and scheduled tasks), then run Finalize via OSOT to clean up.
Shut down the VM and create a recovery point. This preserves the update state and enables rollback if needed. Remove the vTPM again if it was re-added, then create a new template from the updated golden image. Use a naming convention that makes sense for your environment, such as version numbers (Win11-Gold-v2, Win11-Gold-v3) or dates (Win11-Gold-2026-01, Win11-Gold-2026-02).
Important Registration Rules
There are some important rules to keep in mind when updating golden images for Horizon on AHV:
- Every pool change requires a new Nutanix Template for image push: When updating an automated instant-clone desktop pool (installing new applications, applying Windows updates, etc.), perform the changes on the golden image VM, take a new recovery point or create a new template in Prism Central, and then initiate a push image operation in Horizon Console.
- Every agent change requires a new Golden Image registration: If the Horizon Agent or other core agents (like DEM or App Volumes agents) are updated, the agent software needs to be upgraded on the golden image itself. A new snapshot of this updated golden image must then be used to push the change to the pool.
- Every new Golden Image registration requires a new machine name: When creating a new golden image iteration, use a versioned or unique name (e.g., Win11-Gold-Image-v2) to avoid potential Active Directory conflicts. Instant clones get their own unique computer names during provisioning, but reusing the exact same name for a newly registered golden image that was used previously could lead to issues.
The key differences from ESXi workflows are really around the recovery point integration. Instead of managing separate snapshots or clone chains, the Nutanix recovery points provide a clean, integrated way to version golden images. It's one of those quality-of-life improvements that makes day-to-day operations smoother.
What's Next
This post covered the basics of building and maintaining golden images on AHV. In my next post, I'll dive into creating desktop pools, pushing image updates, and rolling back to previous versions using recovery points, along with some gotchas I've encountered during testing.
References
- Omnissa TechZone: Manually Creating Optimized Windows Images for Horizon VMs
- Omnissa Docs: Preparing a Golden Image on Nutanix
- Omnissa Docs: Updating a Golden Image on Nutanix
Series Navigation
- Part 1: Omnissa Horizon 8 Architecture on AHV
- Part 2: Horizon 8 Image Management on AHV (this post)
- Part 3: Desktop Pools on AHV (coming soon)
Have questions or feedback? Feel free to reach out to me on LinkedIn or via email at mike@mikedent.io.