Cisco recently patched two critical vulnerabilities in their firewall products, discovered after probable nation-state actors targeted them in a campaign dubbed “Arcane Door”. These zero-day vulnerabilities, found in devices running ASA and FTD software, were exploited to implant malware and possibly steal data. Cisco released three patches and has tracked the hacking group under UAT4356 and STORM-1849 by Microsoft. These flaws, involving HTTP header parsing and a legacy VPN client preloading capability, allowed attackers root-level access, emphasizing the need for immediate patching and security upgrades.
The Talos blog post and more details from Cisco can be found here and here. Thanks to Jarad for the heads up!
Understanding the ArcaneDoor Espionage Campaign: Implications and Defenses
Background
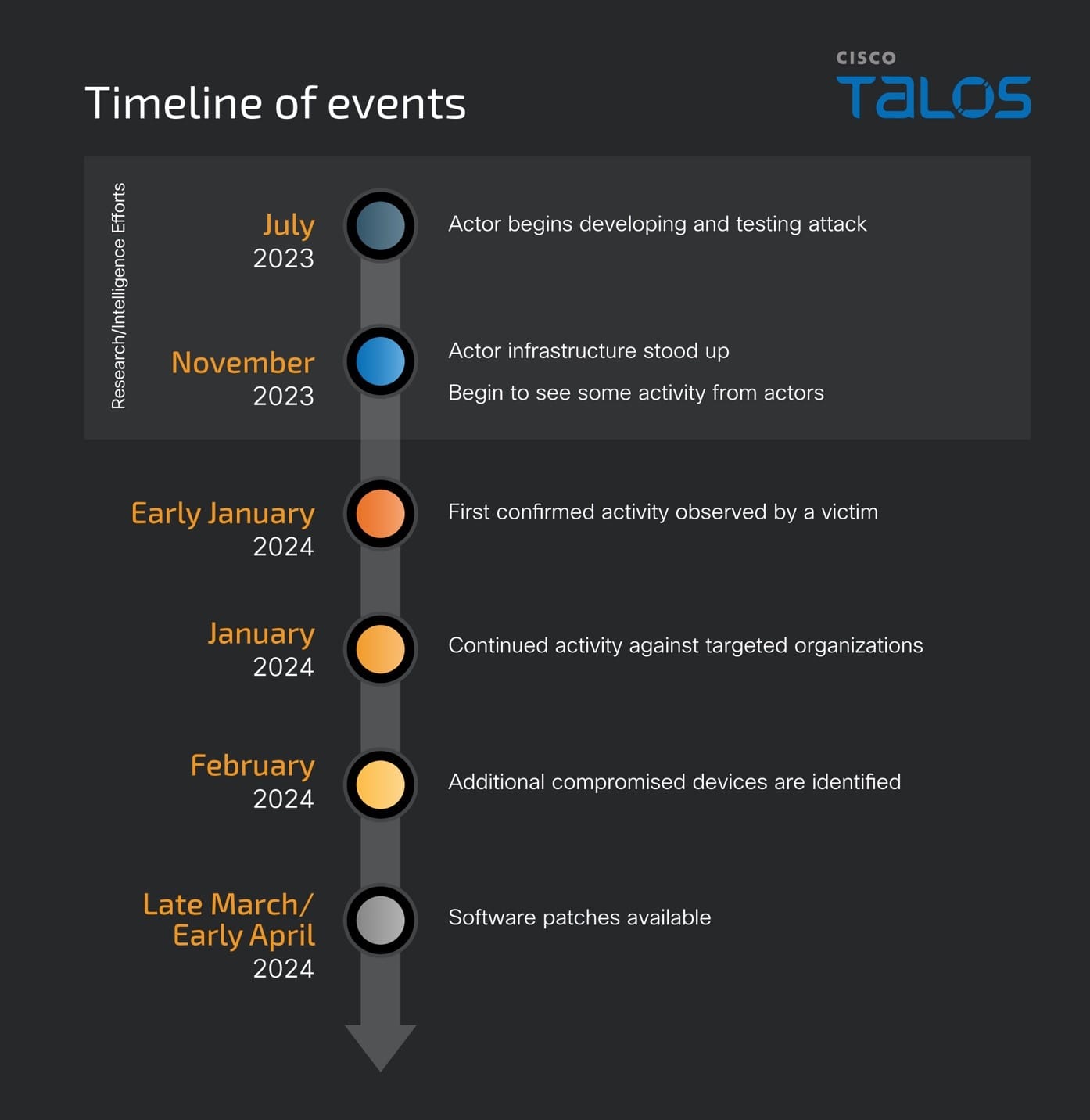
The ArcaneDoor campaign represents a sophisticated espionage effort aimed at exploiting perimeter network devices across various organizations, including critical infrastructure sectors. By targeting devices such as Cisco Adaptive Security Appliances, attackers, identified as UAT4356, leverage custom malware (like “Line Runner” and “Line Dancer”) to modify configurations, capture network traffic, and potentially move laterally within networks. This campaign underscores the vulnerabilities in network devices and the strategic approaches taken by state-sponsored actors to compromise such essential assets.
Fixes Available
Cisco has released fixes for the ASA and FTD platforms (thankfully, FMC doesn’t have any known impact), as workarounds are unavailable for two of the three posted vulnerabilities. CVE-2024-20353 is the most critical, while the other 2 warrant close inspection.
| Cisco Security Advisory | CVE ID | Security Impact Rating | CVSS Base Score |
|---|---|---|---|
| Cisco Adaptive Security Appliance and Firepower Threat Defense Software Web Services Denial of Service Vulnerability | CVE-2024-20353 | High | 8.6 |
| Cisco Adaptive Security Appliance and Firepower Threat Defense Software Persistent Local Code Execution Vulnerability | CVE-2024-20359 | High | 6.0 |
| Cisco Adaptive Security Appliance and Firepower Threat Defense Software Command Injection Vulnerability | CVE-2024-20358 | Medium | 6.0 |
If you’re running ASA or FTD code I’d say, based on the severity of these vulnerabilities they are important enough to get them to the front of the urgent request line, if you’re currently using AnyConnect (SSL or IKEv2) for remote access.
Unfortunately, the fixes are not part of the gold code release for ASA or FTD, with FTD release 7.2.6 being dropped just a little over a month ago. But It’s important enough to get your devices patched!